
Say Goodbye to 2-Year Certificates and Hello to Multi-Year SSL Plans
As of September 1st, 2-year certificates have been replaced by multi-year SSL plans offering similar benefits
September 1, 2020 marked the dawn of a new era for SSL certificates. Multi-year SSL certificates are now history. The only certificates that will be trusted by major browsers will be those with a validity period of 397 days or less. Why 397 days, you ask? That’s one year plus a one-month grace period for renewal.
Don’t panic yet, though. In reality, multi-year SSL certificates aren’t TRULY going away. It’s more a situation of “they are, but they aren’t.” You see, this change was a long time in the making, so Certificate Authorities (CAs) have had ample time to prepare. In response, they’ve introduced new multi-year plans that will provide similar benefits as the old multi-year SSL certificates did but work a bit differently in practice.
So why were multi-year SSL certificates eliminated in the first place? How do the new multi-year plans actually work? And how do you go about implementing them in your organization?
Let’s hash it out.
Shorter Validity = Higher Security
At its core, the goal of the change is to improve security for users of the world wide web (and not to make your life more complicated, even though it may seem that way at first glance). Those that supported the change argued that the shorter the validity period of a certificate, the more secure it is.
There are several key advantages to shorter-term certificates, including:
- A shorter lifespan for keys, which means a shorter lifespan for compromised keys, as well. With shorter certificates, you have a smaller window of exposure if a key is stolen.
- Certificate security updates are rolled out into the wild at a much quicker pace.
- Organizational information is updated on a yearly basis, including company names, addresses, and domains, which translates to increased user trust.
- Automation is encouraged. With a good certificate management system in place, there is no difference in convenience between shorter and longer lifetimes. They are automatically re-issued when needed, regardless of the validity period.
Users will have to do a little bit extra on their end as the switchover is being made, but the trade-off is a higher level of security over the long-term.
What Does It Mean for Your Website?
First off, only public TLS certificates are affected. Private-root and other certificate types (such as code signing certificates, S/MIME certificates, document signing certificates, etc.) are not impacted.
What about certificates issued before the September 1 deadline? Good news: they will remain valid for their original validity period. The only time you’ll notice anything different is if they need to be re-issued. In that case, you won’t lose any of the validity time, but you’ll need to plan to re-issue again if your initial validity period is still greater than 397 days.
The ultimate answer to “what does it mean for your website?” is that you have more frequent certificate expiration dates to consider. Subsequently, it means that proper certificate management is more important than ever. Automated platforms, such as DigiCert’s CertCentral or Sectigo Certificate Manager, can be a huge help with reducing the risk that expiring certificates pose to your organization, but more on that shortly. Now let’s take a closer look at the specifics of the new multi-year SSL plans.
New Plans, Same Benefits
Save Time & Lower Costs with Multi-Year SSL Plans
So does this mean goodbye to multi-year discounts? Nope! You’ll still enjoy cost savings with these new-age multi-year plans. One of the main benefits of the old multi-year SSL certificates was the price-break you received. The more years you bought, the bigger the discount was on a per-year basis. CAs have mirrored this system in the new plans, so fortunately nothing is changing in that regard. You will still be rewarded for buying multi-year certificates. You’re simply pre-paying for certificate usage upfront, so there’s a discount for that.
You’ll still be saving time with the new multi-year plans, too. You only need to purchase the multi-year SSL subscription once, which is an especially useful feature if your organization has any kind of lengthy purchase-approval process in place. So, at the end of the 397-day validity period all you have to do is re-issue the certificate. That’s it. There’s no need to go through all the legwork of making a brand-new purchase.
Here’s an example of what the new multi-year plans look like with DigiCert’s Secure Site SSL product:
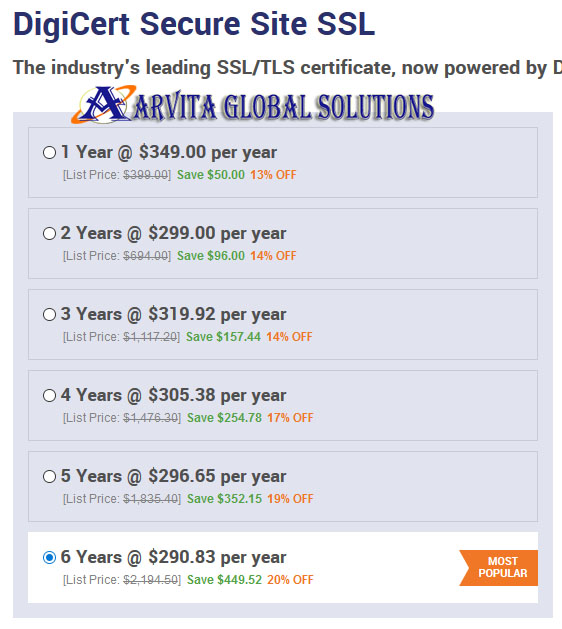
If You Can’t Beat It, Automate It
These plans were also created to further support automation (if it hasn’t been drilled into your head enough yet, automation is a wonderful thing for certificate management). With a certificate management system in place, you don’t even have to worry about the re-issuing task that we were just talking about. All you need to do is setup your system to auto re-issue your certificate every 13 months (or more frequently if you want).
You can implement true automation using DigiCert CertCentral and protocols like ACME. It allows for communication with the CA directly from your server and makes the installation process completely hands-off, requiring no help from the administrator. ACME works for OV and EV certificates and allows for both 1-year and shorter, custom validity periods. It is anticipated within the industry that certificate lifespans will continue to shorten, and by investing the time to setup automation now you can ensure you’ll be ready.
The screenshot below shows the process for adding an ACME directory URL in CertCentral, as well as the ability to input your own custom validity period: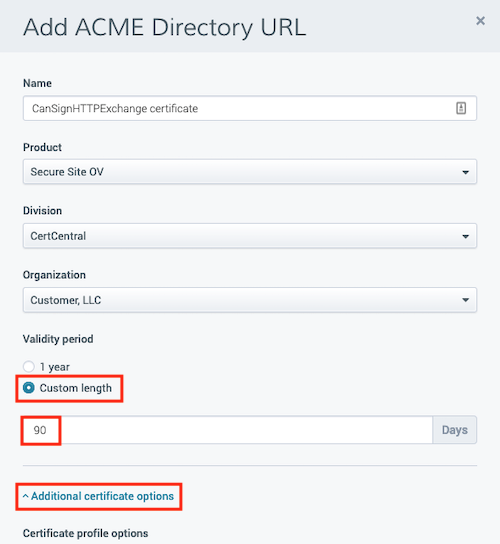
Using automation protocols like ACME is faster and easier than the manual method, and it eliminates the threat of unanticipated certificate expirations. Your costs will be lowered as well, since your staff won’t have to spend their time performing the tedious, time-consuming certificate management tasks. You’ll expose yourself to less human error and will be able to recover from any security incidents more quickly and easily. If you’ve been putting off implementing an automated certificate management platform, now is a great time to do so.
A Real-World Example
Now let’s take a closer look as to how multi-year SSL plans work in practice. Say you’ve just purchased a new 3-year DV certificate plan. How exactly does it work? What all do you need to do on your end to stay secure?
When you first issue the certificate, it will be issued with a validity period of 397 days. Whether you have an automated system in place or not, you’ll be getting an email notification from your CA/certificate provider in advance of the certificate expiration. If you’re manually managing your certificates, then you’ll especially want to pay special attention to these reminders.
So, let’s say you just got a 30-day expiration reminder. At that point, you’ll have 30 days to re-issue (free of charge, of course) the certificate and complete domain validation.
Once you’ve done that, you’ll instantly get a new certificate that’s valid for another 397 days. Basically, you’ll keep repeating the process until the overall validity time is used up.
As far as the logistics of the purchase itself, you have a few different options. As before, you can buy multi-year SSL certificates via our website, API or through integrations like WHMCS.
A Step in the Right Direction
The move away from multi-year certificates is something that has been in the works for years. It’s a change that will require a bit of extra action from users at the front-end, but one that will ultimately translate to a higher overall level of security for websites and users alike.
With shorter validity times across the board, effective certificate management is also more important than ever. The increased adoption of automated systems is expected, which will hopefully lead to a drop in costly expired certificate incidents over the long-term.
And luckily for you, the website admin, CAs and the rest of the SSL industry were well-prepared for the September 1 deadline. With the new multi-year subscription plans in place, customers can still receive the same benefits and cost savings that they got with the old multi-year SSL certificates.
Overall, it’s a change that might seem intimidating at first glance, but one that is proving to be a win-win for all involved.



